|
|
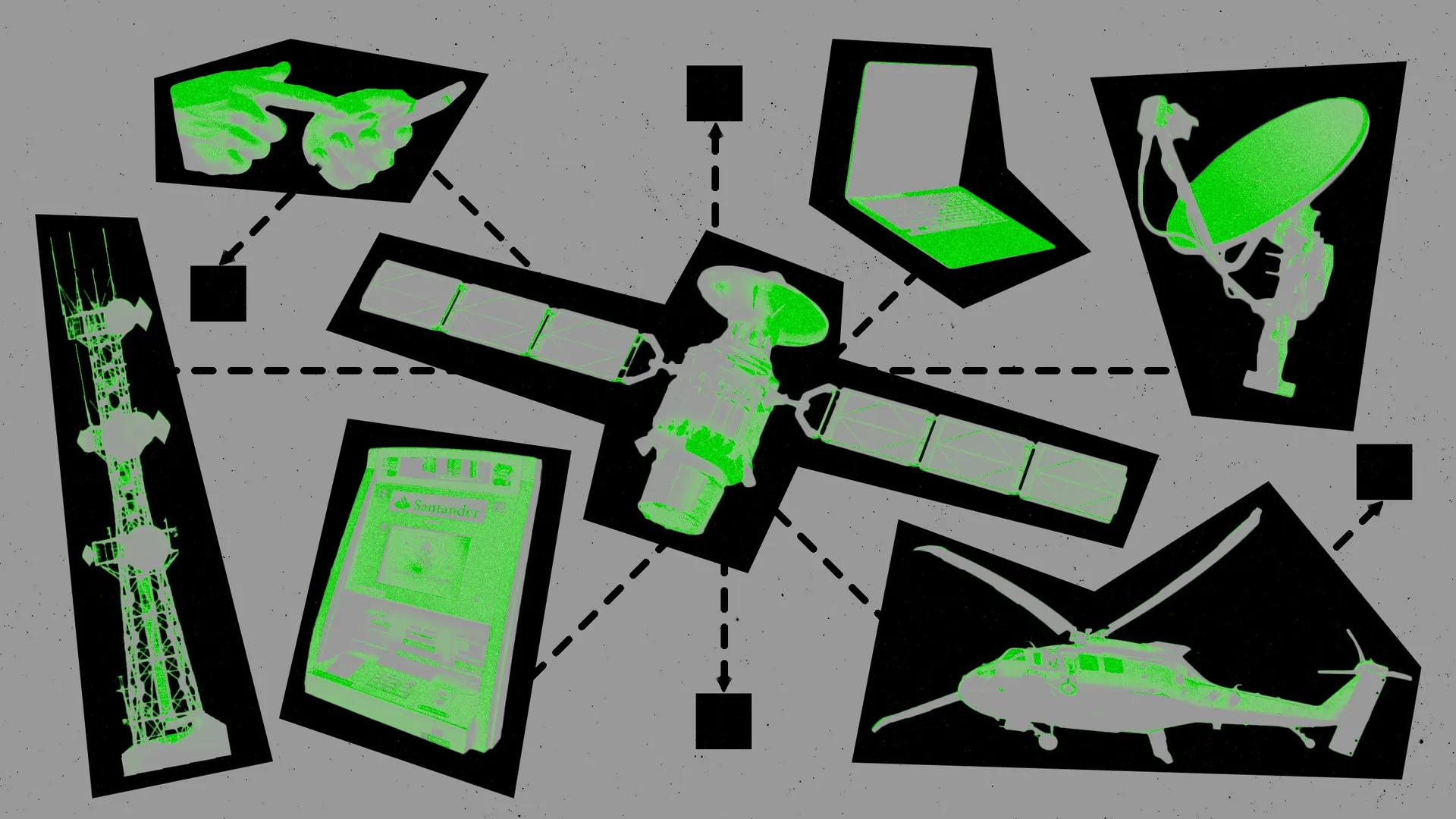
"The fact that this much data is going over satellites that anyone can pick up with an antenna is just incredible."
— Aaron Schulman, professor at UC San Diego
|
|
Welcome back to Snippets 👋 Here's what's been happening at the intersection of privacy, AI, and tech:
- Study finds significant portion of satellite traffic is unencrypted
- An expert makes the case against Europe's 'Chat Control' law
- California shields immigrant street vendors from federal scrutiny
- And so much more!
|
|
|
|
|
Satellite communications leaking unencrypted data
|
 |
|
Photo-illustration: Jacqui VanLiew; Getty Images
|
With $800 in off-the-shelf equipment, researchers from UC San Diego and the University of Maryland revealed that space-to-earth satellite communications are leaking a significant amount of sensitive data.
|
- In just nine hours, the researchers collected more than 2,700 T-Mobile phone numbers, captured one side of users’ calls and text messages, and gathered communications involving critical infrastructure, law enforcement, and the military.
- To do so, they pointed a dish installed on the roof of a UC San Diego building at different satellites—exposing clear vulnerabilities in the satellite communications industry's cybersecurity strategy.
- Some carriers, like T-Mobile, quickly encrypted their communications after the disclosure. Others, including critical U.S. infrastructure operators, still have not.
- And with only 15% of global satellite traffic analyzed in the study, researchers believe even more data remains exposed.
|
|
|
|
|
|
|
Inside the mind of a CPO: Lessons from Sue Vinci
|
|
In this episode of Transcend Field Trips, our Field CPO Ron De Jesus, sits down with Verizon's Chief Privacy Officer, Sue Vinci, who brings over two decades in privacy leadership to one of the world’s largest telcos.
Sue details the essential shift from viewing privacy as a regulatory burden to embracing it as a business imperative. Watch the full episode below to get clear strategies on how to govern with confidence while unlocking the next stage of your privacy program’s evolution.
|
|
|
|
|
|
|
|
Opinion: ‘Chat Control’ law protects neither children nor democracy
|
 |
|
Photograph: Andrew Brookes/Getty Images/Image Source
|
Europe’s proposed ‘chat control’ law would require service providers to scan all communications and files for “abusive material”—a move that Jeremy Malcolm, chair of the Center for Online Safety and Liberty, argues is an overreach that does not address the root problem.
|
- The ‘chat control’ law reflects a larger trend worldwide. In the UK, Apple faced legal action for refusing to install a government backdoor, while age-verification and surveillance mandates have appeared in Australia and several U.S. states.
- While these laws aim to combat Child Sexual Abuse Material (CSAM) and protect minors, overly broad censorship only pushes users underground—fueling adoption of VPNs and privacy-focused browsers like Tor.
- Malcom argues that governments should empower mainstream platforms to voluntarily detect CSAM, rather than draining resources on mass surveillance that undermines both privacy and democracy.
|
|
|
|
|
|
|
|
California shields immigrant street vendors from federal scrutiny
|
 |
|
|
California Governor Gavin Newsom has signed a new law meant to shield immigrant sidewalk vendors from federal immigration enforcement.
|
- The law, which takes effect on January 1, prohibits local governments from inquiring about the immigration status of street vendors or from requesting personally identifiable information without a subpoena.
- As the Trump Administration expands deportation efforts and arrests of illegal US residents, the law reflects similar measures in other Democratic-led states.
- Over 100 immigration-related bills have been passed in the United States this year—with a relatively even split between those expanding immigrant protections and those diminishing them.
|
|
|
|
|
|
|
|
- Google to spend $15 billion on AI data hub in India.
- Texas vacates most of the HIPAA reproductive privacy rule.
- A privacy-first PDF editor to substitute Acrobat.
- To improve your privacy, follow along with Opt Out October.
- Civil society coalition questions the Irish DPC’s independence.
|
|
|
|
|
|
Exploring privacy tools that learn as they go
|
 |
|
|
Researchers from Sweden’s KTH Royal Institute of Technology and Inria Saclay in France have developed a new privacy framework that uses estimated data distributions to improve utility while maintaining strong privacy guarantees.
|
- Using an uncertainty set, the researchers modeled all plausible data distributions—designing mechanisms that meet a chosen privacy level for each.
- The framework connects large-deviation theory to practical application, offering formulas that relate sample size, desired privacy levels, and failure probability.
- In binary data tests using Laplace and Gaussian mechanisms, the pointwise maximal leakage (PML) design produced higher-utility data by requiring less noise while maintaining high privacy guarantees.
- However, the approach has limitations. When applied to high-dimensional medical data, such as DNA sequences, it may be more susceptible to errors in distribution estimation.
|
|
|
|
|
|
|
|
Experts concerned routine exposure could normalize public surveillance
|
 |
|
Illustration: Brendan Lynch/Axios
|
According to a 2024 study co-authored by Boston University law professor Woodrow Hartzog, gradual, low-level monitoring is dulling public resistance and normalizing constant tracking.
|
- The study distinguishes "privacy nicks," low-level, tolerable intrusions, from "privacy chops," or dramatic violations—arguing that legislation disproportionately targets chops while overlooking nicks.
- As these routine intrusions accumulate, individuals grow resigned to being watched, shifting their perspective on what might be considered invasive.
- Public resistance has at times forced cities to pause or roll back surveillance systems, but such reversals are rare and require sustained pressure and strong advocacy to produce results.
|
|
|
|
|
|
|
The definitive guide for switching off OneTrust
|
|
In this expert-driven guide, see best practices for moving off a legacy platform and onto a modern solution built for today's privacy landscape. It’s a roadmap for privacy professionals who know it's time to switch but need a clear plan to get their organization on board, including:
- The most common signals it's time for a change
- A strategic playbook for gaining cross-functional buy-in
- A comprehensive timeline for your migration + how to prepare for the process
- Why modern privacy platforms make migration worth it
|
|
|
|
|
|
|
|
|
Snippets is delivered to your inbox every Thursday morning by Transcend. We're the platform that helps companies put privacy on autopilot by making it easy to encode privacy across an entire tech stack. Learn more.
|
|
|
|
You received this email because you subscribed to Snippets. Did someone forward this email to you? Head over to Transcend to get your very own free subscription! Curated in San Francisco by Transcend.
|
|
|
|
|
|